In today's increasingly interconnected world, traditional perimeter-based security models are proving inadequate in the face of sophisticated cyber threats. The rise of remote work, cloud computing, and mobile devices has blurred the lines of the traditional network perimeter. To address these evolving threats, organizations are adopting a zero-trust security model.
Understanding Zero Trust
Zero trust is a security paradigm that assumes no user or device should be implicitly trusted, regardless of their location within or outside the organization's network. It operates on the principle of "never trust, always verify," requiring continuous authentication and authorization for every user 1 and device accessing resources.
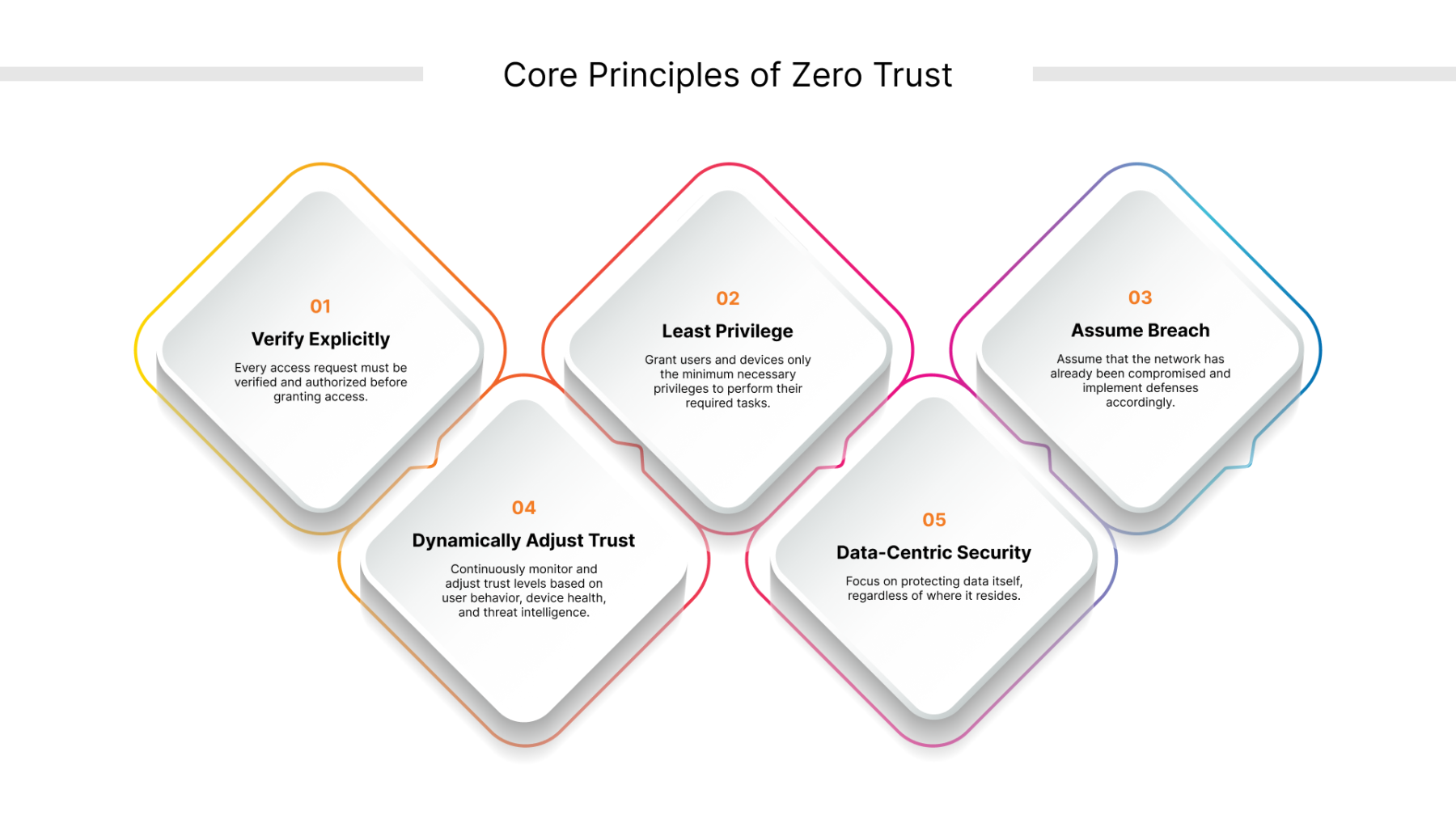
Core Principles of Zero Trust:
-
Verify Explicitly: Every access request must be verified and authorized before granting access.
-
Least Privilege: Grant users and devices only the minimum necessary privileges to perform their required tasks.
-
Assume Breach: Assume that the network has already been compromised and implement defenses accordingly.
-
Dynamically Adjust Trust: Continuously monitor and adjust trust levels based on user behavior, device health, and threat intelligence.
-
Data-Centric Security: Focus on protecting data itself, regardless of where it resides.
Implementing a Zero Trust Model
Implementing a zero trust model requires a multi-layered approach:
-
Identity and Access Management (IAM):
-
Strong Authentication: Implement multi-factor authentication (MFA) for all users, including biometrics, one-time passwords, and hardware tokens.
-
Least Privilege Access: Grant users only the necessary permissions to perform their job functions.
-
Continuous Authentication: Re-authenticate users periodically to ensure ongoing authorization.
-
Network Segmentation:
-
Microsegmentation: Divide the network into smaller, isolated segments to limit the impact of a potential breach.
-
Software-Defined Perimeter (SDP): Create secure connections to resources based on user identity, device health, and application requirements.
-
Endpoint Security:
-
Endpoint Detection and Response (EDR): Deploy EDR solutions to detect and respond to threats on endpoints.
-
Antivirus and Antimalware: Implement robust endpoint security solutions to protect against malware and other threats.
-
Device Posture Assessment: Continuously assess the security posture of endpoints, including software updates and security patches.
-
Data Loss Prevention (DLP):
-
Implement DLP solutions to prevent the unauthorized exfiltration of sensitive data.
-
Data Encryption: Encrypt data both in transit and at rest.
-
Data Classification: Classify data based on sensitivity and implement appropriate security controls.
-
Cloud Security:
-
Cloud Access Security Broker (CASB): Utilize CASBs to control and monitor cloud access.
-
Cloud Security Posture Management (CSPM): Continuously monitor and assess the security posture of cloud environments.
Benefits of Zero Trust
-
Enhanced Security: Reduces the risk of data breaches and cyberattacks.
-
Improved Visibility: Provides better visibility into network activity and user behavior.
-
Enhanced Agility: Enables faster response to security threats.
-
Improved Compliance: Helps organizations comply with industry regulations and data privacy standards.
Challenges and Considerations
-
Complexity: Implementing and managing a zero trust architecture can be complex.
-
Cost: Implementing and maintaining zero trust solutions can be costly.
-
Change Management: Requires significant organizational change management to adopt a zero trust approach.
-
Skill Requirements: Requires specialized skills and expertise to design, implement, and manage a zero trust architecture.
Conclusion
In today's threat landscape, a traditional perimeter-based security approach is no longer sufficient. By adopting a zero trust security model, organizations can significantly enhance their security posture and protect their valuable assets from cyber threats.


